The U.S. Government Charged Russia’s Most Destructive Hackers
October 19, 2020The US government accused six members of Russia's military intelligence of being behind the destructive NotPetya ransomware attack.
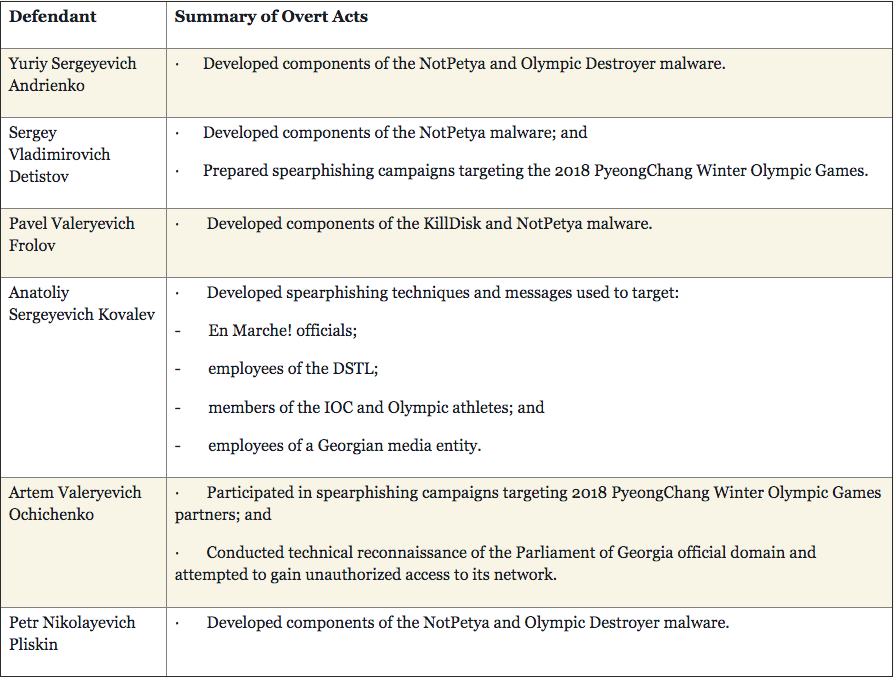
The Department of Justice announced the indictment of six people who are allegedly part of the Sandworm hacking group, responsible for a slew of high-profile hacks in the last few years—"the most disruptive and destructive series of computer attacks ever attributed to a single group,” as the DOJ put it. They are most famous for unleashing NotPetya, a ransomware that wiped thousands of computers all over the world.
Prosecutors believe the hackers are all part of Unit 74455 of the Russian Main Intelligence Directorate, better known as GRU.
They all became part of the FBI's most wanted list of cyber criminals on Monday.

The indictment of the six alleged hackers and spies also doubles as the first official document that accuses the Sandworm hacking group—widely believed to be working for the Kremlin—of some of the most impactful data breaches and hack and leak operations of the last decade.
"No country has weaponized its cyber capabilities as maliciously or irresponsibly as Russia, wantonly causing unprecedented damage to pursue small tactical advantages and to satisfy fits of spite," Assistant Attorney General for National Security John Demers said in a press release. "Today the Department has charged these Russian officers with conducting the most disruptive and destructive series of computer attacks ever attributed to a single group, including by unleashing the NotPetya malware."
As John Hultquist, the Senior Director of Intelligence Analysis at FireEye, noted on Twitter, we now know, with pretty high confidence, that Sandworm was behind the last minute leak of emails stolen from the Emmanuel Macron campaign in 2017, the attack on the Pyeongchang olympics, the blackouts in Ukraine, and, of course, NotPetya.
"Today's indictments are a laundry list of Sandworm's misdeeds, some of which were never officially recognized until now," Hultquist, who has tracked Sandworm for years, wrote on Twitter. "They are the most aggressive actor I have ever encountered and they have been my greatest concern for the upcoming election."
As cybersecurity and intelligence expert Roel Schouwenberg argued in a Motherboard op-ed last year, NotPetya was a watershed moment in the history of government hacking.
"NotPetya ushered in a new era of implant-enabled warfare where public opinion is as much the target as traditional IT systems. This wasn’t 'hack and leak' or 'inauthentic amplification' on social media. This is information operations by using malware to create a narrative, and shows what the future of conflict looks like: one where malware not only disrupts our business operations but also targets our minds and influences media coverage," Schouwenberg wrote at the time. "NotPetya created significant downtime and a whopping $10 billion in damages, but its most subversive impact was how it deceived the public."
In 2017, after NotPetya damaged hundreds of thousands of computers all over the world, the hackers tried everything they could to muddy the waters and pretend it was just a simple ransomware attack. At the time, we spoke to the hackers and they decrypted a file infected with the NotPetya malware. The hackers did this experiment to prove that their malware was not really intended to lock computers forever, which could be seen as a destructive cyberattack, as opposed to a classic ransomware scheme where hackers attempt to export money from victims.
The six hackers are accused of multiple hacking crimes and racking up an estimated $1 billion in damages for U.S. organizations that were hit by NotPetya. They are all in undisclosed locations, and as many others Russian and Chinese government hackers indicted by federal prosecutors, they may very well never even set foot in the US.
Would you like to read more stories about hacking, privacy, and surveillance? Subscribe to our pop-up 'zine The Mail. The next issue is about hacking culture.
