Vulnerability Exposed Microsoft Azure Users to Cyberattack
August 7, 2019New data from Check Point Research says dozens of vulnerabilities found in a commonly used protocol left millions of Microsoft cloud users open to attack.
In a presentation this week at the Black Hat security conference in Las Vegas, the firm noted that flaws in the Remote Desktop Protocol (RDP)—routinely used to access remote Windows machines—could be exploited to execute arbitrary code on a target’s system, allowing them to view, change, and delete data or create new accounts with full administrative rights.
RDP was originally developed by Microsoft, and is frequently used by users looking to connect to a remote Windows machine. There’s several popular open-source clients for the RDP protocol utilized by Linux and Mac users as well.
Last February Check Point revealed 25 RDP vulnerabilities an attacker could use to compromise an IT professional or security researcher’s computer. These vulnerabilities impacted open source RDP clients like FreeRDP, but also rdesktop (the RDP client included in distros of Kali Linux) and the Windows client: mstc.exe.
“Once we have a direct channel back to your to your machine, we can practically do anything we want on that machine,” Checkpoint’s Yaniv Balmas said at the time. “We can do everything we want. The machine is ours."
Check Point’s new research indicates that these vulnerabilities also opened the door to even broader attacks on customers of Microsoft’s Azure cloud computing platform. According to Check Point’s latest findings, Microsoft’s Hyper-V Manager—used to help manage remote virtual machines via a graphical user interface (GUI)—was also vulnerable to attack.
“Any user that connects to or works on a Windows machine in the cloud, or uses Microsoft's local Hyper-V virtual machines, could be a possible target of the attack that we described and demonstrated,” Check Point researcher Eyal Itkin told Motherboard.
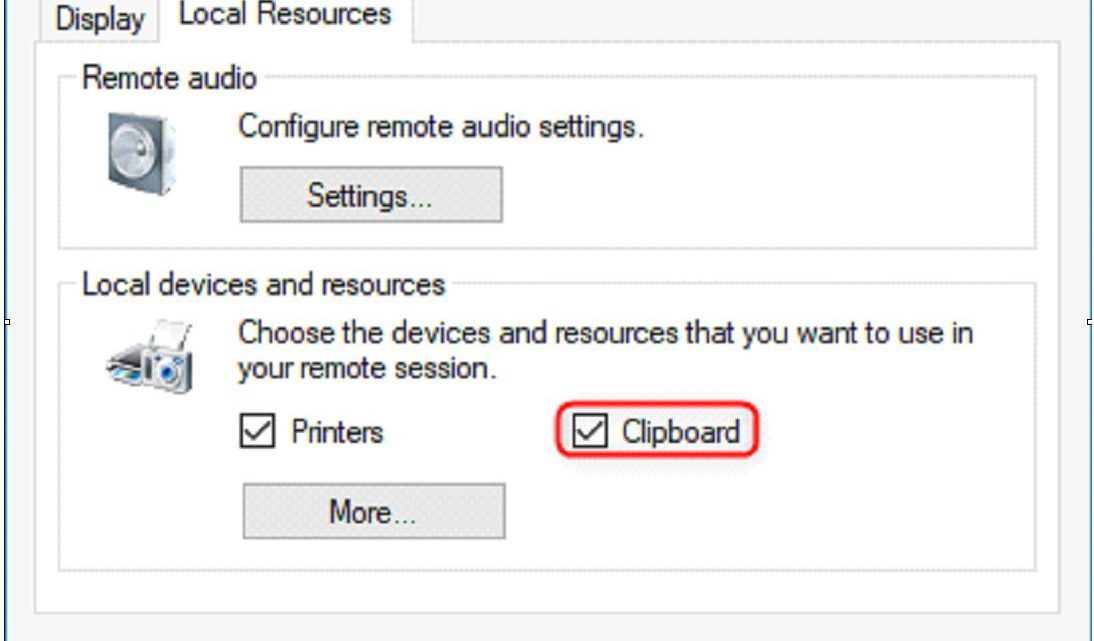
Itkin told Motherboard that despite not being an RDP client itself, Mcrosoft’s Hyper-V manager uses many of the same vulnerable backend resources (like clipboard synchronization, which allows you to copy and paste content across devices), and even the same graphic user interface (GUI):
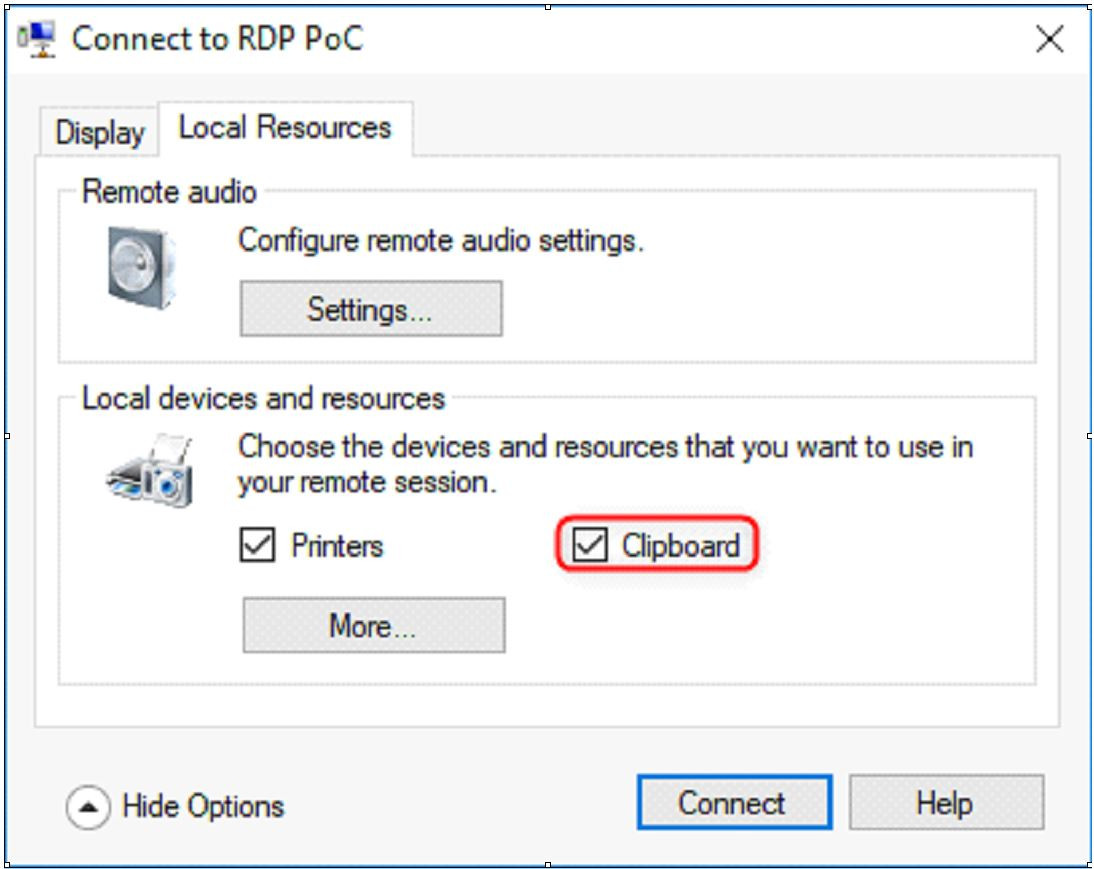
In Check Point’s original findings, the firm found that by abusing the “copy & paste” feature over an RDP connection, a malicious RDP server could transparently drop arbitrary files to arbitrary file locations on the client’s computer, opening the door to all manner of mischief. By relying on many of the same technologies, Hyper-V Manager was also vulnerable.
https://youtu.be/F70FGv_QxDY
“As the saying goes: your system is only as strong as its weakest link,” Itkin said. “In other words, by depending on other software libraries, Hyper-V Manager inherits all of the security vulnerabilities that are found in RDP, and in any other software library that it uses.”
Check Point was quick to note that 57% of Fortune 500 companies currently use Azure, and Windows 10 can currently be found running on around 45.8% of the world’s PCs, making the scope of the vulnerability’s potential impact significant.
While the open source community quickly patched the RDP vulnerabilities in its clients, Microsoft did not patch mstc.exe. It told Check Point last February that while the company’s concerns were valid, they did not reach Microsoft’s “bar for servicing.” That said, Microsoft was quick to issue a patch and CVE (Common Vulnerabilities and Exposures) alert after Check Point informed the company of this newer problem with Hyper-V manager.
“A security update was released in July,” Microsoft told Motherboard in a statement. “Customers who apply the update, or have automatic updates enabled, will be protected. We continue to encourage customers to turn on automatic updates to help ensure they are protected.”
The company did not respond to questions asking why it felt the previous RDP vulnerabilities did not warrant the same level of attention.
“We were disappointed by their initial response, and once we told them about the connection to their Hyper-V products, we immediately received a different response, ending in them recognizing this as a vulnerability, and eventually releasing a patch for it,” Itkin said.


